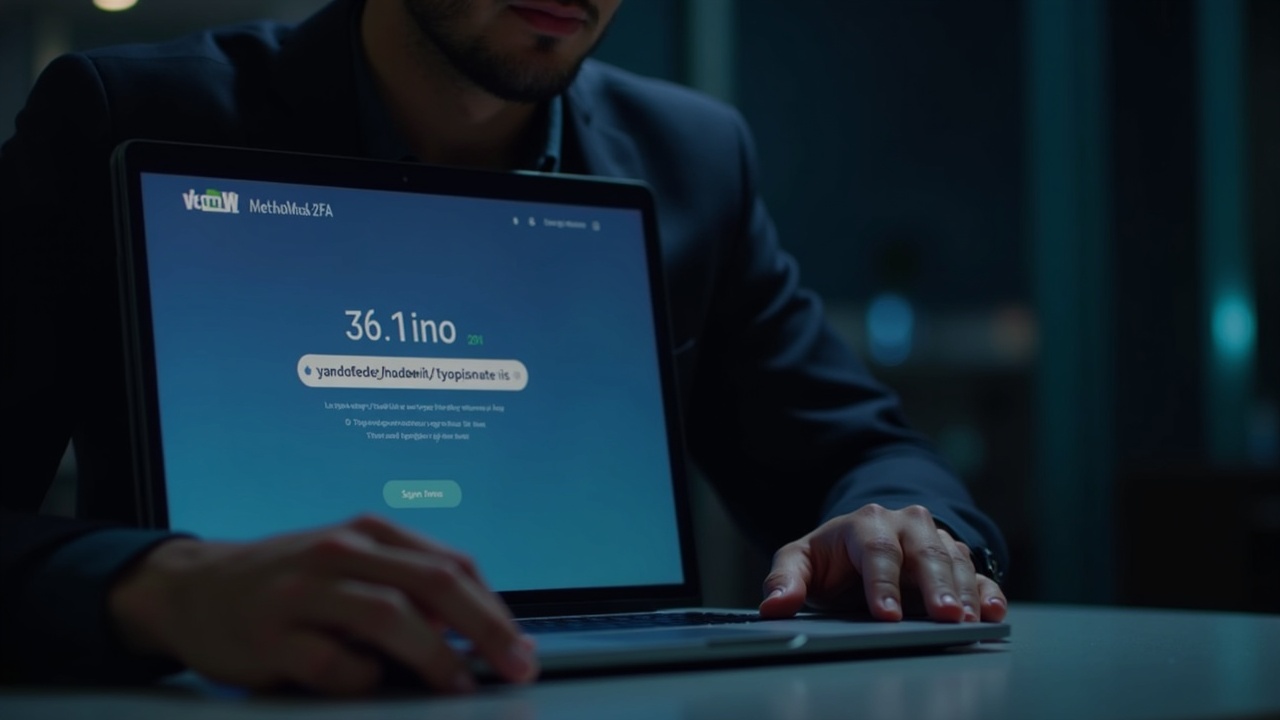
SlowMist reported that on Jan. 5, 2026, attackers ran a coordinated phishing campaign that used counterfeit two-factor authentication (2FA) prompts to steal MetaMask recovery phrases and trigger rapid, automated wallet drains. On-chain investigators flagged aggregate losses exceeding $107,000 across hundreds of EVM wallets, with individual thefts typically ranging from $500 to $2,000.
The campaign blended domain impersonation, realistic UI elements, and urgency-driven social engineering to bypass basic user verification. The operational impact is that wallet availability and end-user custody integrity can fail quickly once a recovery phrase is surrendered.
🚨MetaMask 出现新型 '2FA 安全验证' 骗局 @MetaMask @tayvano_
注意防范 pic.twitter.com/RJM78If9zb— 23pds (山哥) (@im23pds) January 5, 2026
How the Phishing Flow Worked
Attackers initiated the sequence through unsolicited messages delivered via email, social posts, or compromised webpages, presenting them as official MetaMask security alerts. The initial touchpoint was engineered to look like legitimate security outreach while directing users into a controlled funnel.
Fraudulent domains used typosquatting and homograph techniques to resemble metamask.io, then redirected victims into a counterfeit 2FA verification flow designed to mimic a real security check. The campaign’s leverage came from URL-level deception that made the destination appear authentic at a glance.
The fake interface added countdown timers and explicit warnings to create immediate pressure, pushing users to act without verification. The objective was explicit: coerce users into entering 12- or 24-word recovery phrases.
Once victims entered the phrase, malicious client-side scripts captured it and automated wallet imports, enabling near-instant transfers of assets to attacker-controlled addresses. The value chain was optimized for speed, converting a single compromised phrase into irreversible loss within minutes.
SlowMist’s Chief Information Security Officer summarized the playbook: “scammers create fake MetaMask security pages to trick users into completing a fraudulent two factor authentication (2FA) process.” The core tactic was a tight coupling of credible impersonation with high-pressure user prompts.
From an infrastructure and operational-security perspective, the campaign targeted human verification steps rather than consensus or client-level protocol weaknesses. This is a user-layer compromise, meaning technical resilience cannot prevent loss once private keys are exfiltrated.
Mitigation Priorities for Wallet and Platform Teams
Enforce strict URL hygiene by using trusted bookmarks or manually typed addresses and improving browser or extension detection of homoglyph domains.
Harden user endpoints by recommending hardware wallets for high-value accounts so private keys remain in a secure element and transfers require physical confirmation.
Adopt phishing-resistant MFA for ancillary accounts and prioritize FIDO2/WebAuthn hardware keys or authenticator apps over SMS OTP.
Revoke unnecessary token approvals and avoid unlimited allowances, then operationalize token-approval monitoring in security playbooks for dApp teams.
Keep clients and extensions current and audit third-party browser extensions to reduce interception and redirection risk.
These controls reduce exposure at the client integration layer and limit how fast a leaked recovery phrase becomes a completed theft. The practical objective is to introduce friction for attackers while preserving a clean, verifiable user journey.
Looking ahead, the incident will test how quickly client teams, browser vendors, and domain-abuse monitoring services can detect typosquatting registrations and block active phishing kits. The operational priority is tighter domain telemetry, better approval analytics, and faster surfacing of anomalous transaction patterns to reduce attacker success rates.